Cyber Attacks are increasing day by day. Nowadays hackers are targeting anybody from anyplace. Here I show you how can your protect yourself from hackers and cyber criminals.
We collect best tips and tricks for you in this post. Read this post and follow all steps for securing your Computer and your online activities.
Top 15 Tips To Protect Yourself From Hackers
Every computer user needs to know the basic things to keep their device and data secure. Given below are the few tips and habits that can help you:
1. Make Your Phone’s Lock Code More Secure
Many of us consider that the default 4-digit PIN is the most secure locking code. However, it is not. It is always better to add an extra digit to make your phone more secure. For iOS and Android, go to settings and add one more digit to make your phone’s lock code more. Further, Android also has lock screen tools that lets you enhance your phone’s security.
2. Look Out for Social Engineering Attacks
Social engineering is the biggest security concern these days, as cyber thieves and hackers smartly gain access to your secure information either through mimicking other companies, phishing, and other common strategies. You need to be careful of all the suspicious phone calls, emails, links and other communications that you receive. Also, it is known that most of the data breaches come from internal sources. Hence, awareness is the important key, as it may be astonishing to know that even security experts can be easily tricked or hacked into.
3. Lock Down Your Wireless Router
The first line of defense for your home network is your router. To keep your Wi-Fi secure, you need to change the router’s administrator login, use WPA2 (AES) encryption, and change other basic settings.
 |
| Wifi Router Reset Button |
Read More: How To Secure Home Wifi Network
4. Don’t Use Public Wi-Fi Without A VPN
While using public Wi-Fi, it is important to use a network that has security. To stay safe on public Wi-Fi networks, your best defense will be to use a VPN (Virtual Private Network), which keeps you safe even in other conditions too.
5. Be careful while using thumb drive
Thumb drives, also known as flash drives, are small and easy storage devices to use across different computers. They are a popular device that people use to exchange files and documents. They can also spread viruses easily across computers and networks.
 |
| Be careful with thumb drive |
6. Try not to use public computers
For many people, not using a public computer can be difficult. Those without a computer or Internet access at home often use Internet cafes to get online. However, the more different people use a computer, the more likely a virus has infected it.
7. Clear your browser history
This goes for all the devices you use in a day – your home computer, your work computer, or your friend’s iPad. Internet browsers like Firefox or Chrome keep track of where you’ve been and what you’ve done online. They keep records of every site you visited. Information about what you sent from or saved on your computer can be kept for days or weeks. It is very easy for anyone who sees that information to steal a detailed record of your online activities.
8. Use Strong Passwords
Password are your first line of defense in this digital war between hackers and the potential victims. If I can get your password, the rest is easy. Create strong Passwords password generator website.
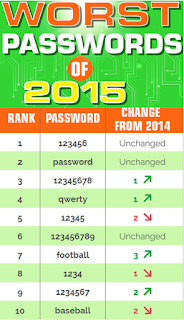 |
| Worst Password of 2015 |
Use this website to generate strong password.
9: Use Two-Factor Authentication
Two-factor authentication offers the extra layer of security that protects you in case your password gets stolen. Turn this feature on in all the places where you can use TwoFactorAuth. Further, if you lose your phone (most often used as the authentication device), you can still get back into your account if you plan ahead.
 |
| Two Way Authentication |
10: Never Click on Suspicious Links
I hope this is superfluous information, but NEVER click on a link sent to you in an email. I don’t care if it came from what appears to be trusted sources, such as your bank or friend, NEVER click on a link in your email. It is so easy for me to embed malware in that innocuous looking link that it is child’s play.
11: Do Not Use P2P File Sharing Networks
Hopefully, this only applies to a few of you. Do NOT do use peer-to-peer file sharing sites. For the uninitiated, peer-to-peer (or P2P) file sharing is the uploading and downloading of music, videos, TV shows, movies, documents, and more from one computer to another without using a centralized server.
Music, movies, documents, and other files are really easy to embed malware in. This means that when you download files from P2P networks, you are giving me easy access to your system. In reality, nearly all of these files have malware in them. I can guarantee you that if you have downloaded at least one file from P2P, that your machine is infected with malware, probably irretrievably.
12: Keep Your System & Apps Updated
New security vulnerabilities (holes) are being discovered daily in your operating system (Windows 7 or 8, Linux, Mac OS X) and your applications (Word, Excel, Flash, IE8, Adobe Reader, etc.). When these vulnerabilities are found, hackers like me then develop a way to exploit that vulnerability.
Soon these “exploits” are passed around to other hackers and everyone is trying to use them against you. This then allows us to install our software on your system to control it and steal your resources and information
When the software developers such as Adobe, Microsoft, and Apple learn of these vulnerabilities, they then develop “patches” to close these security holes. They release these patches in the updates they offer you, sometimes daily. You must update to be secure!
13: Use Antivirus Products & Keep Them Up to Date
Once again, I hope this piece of advice is superfluous. Everyone should have some form of antivirus software on their system. AV software is not perfect, but it is certainly better than nothing.
Even the best AV software is effective on about 95% of KNOWN malware (AV software is totally ineffective against unknown or zero-day malware). That means that one in 20 pieces of malware will be missed. Some of the lower quality AV software will miss 1 in 2 pieces of malware. In addition, AV software is only effective if its activated and updated, so make certain to update its signatures daily.
14: Use a Really Good Firewall
Although Microsoft ships a rudimentary firewall with its operating system, I strongly suggest that you install a third-party firewall for better protection.
There are many third-party software firewalls out there, some better than others, but I want to suggest Zone Alarm’s Free Firewall. As the name says, it is free and very effective. Not only does it block outsiders from getting in, but it also stops malware from accessing resources on your computer and talking out (hackers need to control the malware, so the malware must be able to communicate OUT to be effective).
If you follow the above procedures, you will always be safe surfing the Internet.
If you like this article then please share it and comment here bellow section.

0 coments ::
Post a Comment